A security vulnerability was discovered at GitHub back in 2012 that made it possible for an attacker to add new SSH keys to arbitrary GitHub user accounts. Although there was no known malicious activity using this exploit, they took the responsible step to email all their users that have SSH keys associated with their account to verify and approve them before they could be used to clone/pull/push repositories over SSH again.
That special GitHub audit page for the incident looked like this at the time:
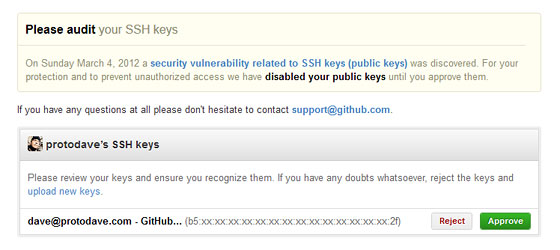
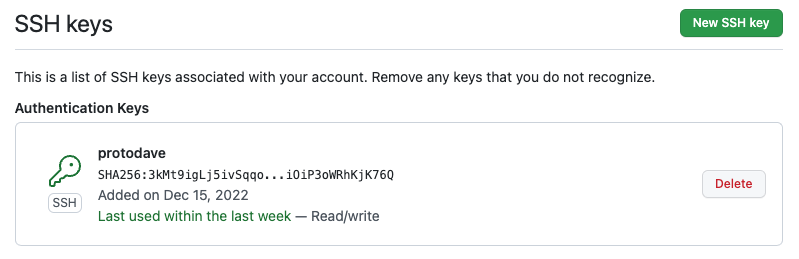
Now, the GitHub SSH Keys page looks like this in 2022:
How to Get a SSH Public Key’s Fingerprint
Here’s a quick reminder of how to get the fingerprint of your SSH public key using the ssh-keygen command. Use the name of your local public key file that you want to check, like so:
$ ssh-keygen -lf id_protodave_github.pubThe resulting fingerprint will look like for an older 2048-bit RSA public key and MD5 hashing:
2048 b5:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:2f protodave@github (RSA)
Or like this for a newer 4096-bit RSA key hashed using SHA256:
4096 SHA256:mXnUMqCAEOZPx...3dDYBxhf5PUOBLI protodave@github (RSA)
Or like this for a newer Ed25519 variant of EdDSA (Edwards-curve Digital Signature Algorithm):
256 SHA256:3kMt9igLj5ivSqqo...iOiP3oWRhKjK76Q protodave@github (ED25519)
If this fingerprint of the local trusted copy of your SSH public key matches the one GitHub shows you, then you are safe and good to go!
How to Generate a New SSH Key-Pair for GitHub
If they don’t match, well, you probably need to figure out why! And then at the very least, delete the key in GitHub and generate a new pair. It’s also not a bad idea to proactively rotate your Github SSH key occasionally. 🔒
On March 15, 2022, GitHub dropped support for older insecure key types like DSA (ssh-dss). They are still allowing the use of existing RSA keys (ssh-rsa) created before November 2, 2021 using any signature algorithm, but newly generated keys must use a SHA-2 signature algorithm, like SHA-256 or SHA-512.
I’d recommend making a new Ed25519 key-pair, which uses SHA-512:
$ ssh-keygen -t ed25519 -C "email@example.com"Alternatively, if your ssh client doesn’t support Ed25519 yet, you can use still use RSA if your client supports SHA-2:
$ ssh-keygen -t rsa-sha2-512 -b 4096 -C "email@example.com"You’ll be prompted to select a filename and a passphrase, and it’ll create separate public key and private key files. Then back on the GitHub SSH Keys page, click the “New SSH Key” button, and paste in your public key (the contents of the file with the .pub extension.)
Getting SSH Public Keys from GitHub
You can also directly compare a locally trusted copy of your public key with the one stored on GitHub.
Although you can only view the fingerprint of your authorized public key(s) on your GitHub account’s SSH Keys page, there is a way to access your GitHub-stored public keys (or anyone’s keys… they are public, after all!) via `curl or a browser. Use your own GitHub user name, of course:
$ curl -sL https://github.com/protodave.keysDigitalOcean provides cloud products for every stage of your journey. Get started with $200 in free credit!

Dear,
Thanks for the post.
Question, how to control that the local ssh key are already stored in github?