What is DKIM?
DomainKeys Identified Mail (DKIM) is a method for email authentication designed to detect sender address forgery (spoofing) in email, which is often used in spam and phishing emails.
How does DKIM work?
The DKIM system allows email receivers to confirm that a message claiming to come from a particular domain was authorized by the domain’s owner. This means that an email sender can prove that they’re not a spammer.
The email receiver’s system can verify this claim using the an attached digital signature header by looking up the sender’s public key published via a DNS record.
Verifying a valid signature cryptographically also assures the data integrity of the message itself by checking the sender generated hash in the DKIM-Signature: header field.
DKIM For The Masses
Google announced today they have added the ability for Google Apps customers to sign outbound email using the DKIM standard.
You can set it up for your own Google Apps domain (if you are the domain admin) using these instructions.
It’s a simple process but the trickiest part can be creating the DNS TXT record (which contains your DKIM public key), depending on how you manage your DNS. If you are serving DNS directly via your registrar, Google has some specific instructions for popular domain hosts.
Checking your work
Here’s a quick tip how you can check to make sure you created the record properly and it is being served…
From a shell/console (using your own domain name, of course):
dig google._domainkey.protodave.com TXTThis should return the DNS TXT record you created. In my case the response is:
;; QUESTION SECTION:
;google._domainkey.protodave.com. IN TXT
;; ANSWER SECTION:
google._domainkey.protodave.com. 3599 IN TXT "v=DKIM1\; k=rsa\; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCGfiExKCF1qk/JMaESySByrwx2VjPYDZThQa8432pSTf9mj+AtFiY6wo9A4CMMDLfUBzbDhXFzw3s/qci/tTut+sqv+MSAHhCBJV72Kai64j6TjxUUnfW1RkEYvDhXL+9Wy9OODx2DBZeTpPd6N2Rm4ks3b5wvg73s7RCKjTA7XQIDAQAB"Online DKIM Checking Tools
If you don’t have access to a shell and dig, there are also some web-based lookup tools available online:
- DKIM Key Checker (I wrote this one!)
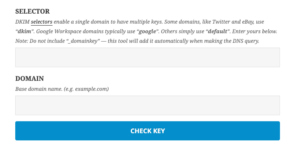
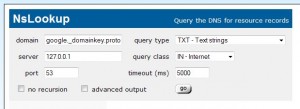
- whatsmydns.net : DNS TXT record checker
Use “google” as the “Selector” and your domain name for “Domain name”

DKIM FAQ
If you’re using DKIM to sign your email, it’s important to make sure that your public key is at least 1024 bits. Keys less than 1024 bits are considered to be cryptographic weak.
DigitalOcean provides cloud products for every stage of your journey. Get started with $200 in free credit!

Thank you
Thanks for this great resource. We use Google apps and I needed to check our TXT record name was correctly setup, this confirmed it was.
Dave,
Thank you very much for the great info and resources… these will now become part of my standard tools.
Dave, thank you.
This is a long shut, but do you have any experience with DKIM and YADIFA (DNS server software)? The TXT record provided by Google does not parse correctly:-
zone.log:2014-05-18 16:20:26.800150 | zone | E | zone load: reading record #46 of zone xxx: PARSESTRING_ERROR
This is the record:-
google._domainkey 86400 IN TXT “v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCzS1CzUSzUHGRw4cz4vVrl2iktW53o2xGK1FzGsSyRT9Rsy8YjMSrTm+ylnUr/MfBz/ixjDI4NDsLuGPHao7g+T96o09sozD+9tMHAgVz8aFgmjdt402wcxCQoK25dKdvTM1droFAYh28qNjg2c6KcULY6224WIljdGhbMEDX/OQIDAQAB”
I haven’t used YADIFA before but I just downloaded the code and took a quick look at the
parse_pstringfunction inlib/dnscore/src/parsing.cwhere those parse errors are being checked. It looks like it should be capable of parsing DKIM TXT records properly, so my guess is that you might just have some accidental special characters pasted into your record. Could you check and make sure you don’t have any newlines, smart quotes or spaces, etc in that record in your zone file?ITs an awesome tool
Thanks for the shell command! It was exactly what I was looking for. (I used “dig -t txt mydomain.com” and it didn’t return the DKIM TXT record, but now I have the right syntax. And the Google Apps-specific example was perfect!)
Any reason that my key looks good in some checkers but others (mx toolbox) can’t find it?
Any idea where i can generate the DKIM key online through a website that (at least) shows some test, and not like “mydkimgen.org” or similar? 😀
There are a lot of generators out there, but most of these pages do not look like you can generate your DKIM there and sleep very well 😀
LOL,
on serverfault people having same thoughts 😀
http://serverfault.com/questions/602080/is-it-safe-to-use-port25-to-generate-dkim-key
Thank you !!
Has anyone used opendikim? I was able to setup this openm and when I look at logs the email gets signed but when I check header on gmail it shows bad format. I’m thinking it’s dns but when i check dns if its the right format it shows OK, so i’m stuck
Any help would help. what is the selector i add to my dns.. for instance.. when i do a test both show vaild records so i’m not sure why i keep getting dkim=neutral (bad format) header.i=@domain1.com header.s=default header.b=lQ1YkIEB;
‘domain1._domainkey.domain1.com:v=DKIM1;k=rsa;p=MIGfMs…………………………..
or
‘domain1.com._domainkey.domain1.com:v=DKIM1;k=rsa;p=MIGfMs…………………………..
@ Dan:
You probably already fixed this issue, but, the issue is your ‘selector’. In your dns TXT record, the ‘selector’ must match your selector in OpenDKIM.
This means in DNS TXT you selected a ‘selector’ called : ‘domain1’
namely : domain1._domainkey.domain1.com
In openDKIM you configured to use a selector called ‘default’
‘header.s=default’
Either configure your DNS to say : default._domainkey.domain1.com
or reconfigure OpenDKIM to use the selector ‘domain1’.